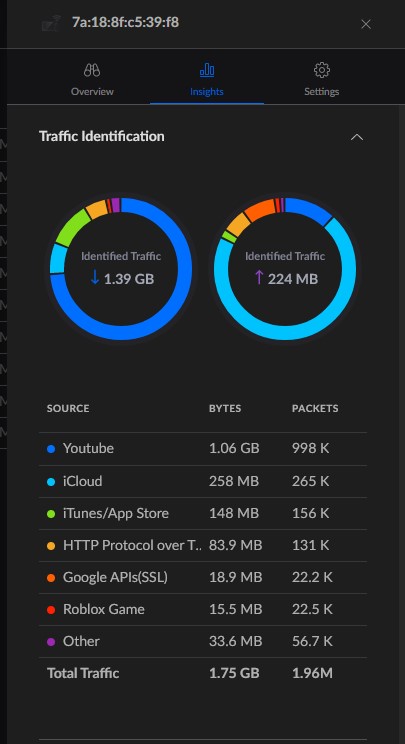
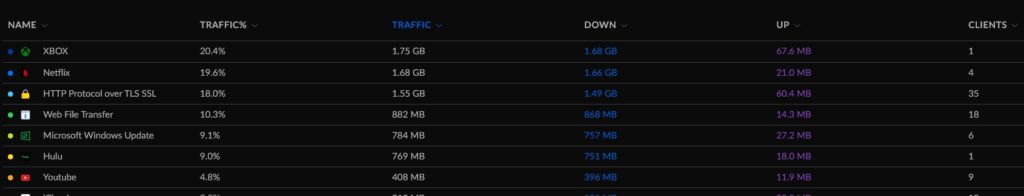
I finally split out my IoT devices onto their own VLAN. That’s it that’s the post. See you all next time!
No, of course I gotta say more. I’m a wordy MFer, after all! But yes, I finally put the IoT stuff on its own network. I should’ve done it a long time ago. It’s been on my list of Homelab to-do’s for like 4-5yrs. A good chunk of not doing it was because I wasn’t sure how to implement it.
I had experimented with VLANs a couple years ago, then doing some basic firewalling to make sure the VLANs and the devices on them couldn’t communicate. I set up a couple VLANs and then created an “RFC 1918” firewall rule to disallow communications between VLANs and their associated subnets. I even have a couple ports tagged on my switches for network isolation purposes.
Lately at work, however, I’ve had some opportunities to play around with and troubleshoot some of the network and firewall issues. So with that better understanding of the Unifi Zone Firewall Policies, I finally pulled the trigger.
I guess I’ll start from the beginning, explaining the three main VLANs I have:
- The Default/Main VLAN. This has my computers, consoles, phones, etc.
- The Guest VLAN. This one is attached to my guest WiFi, naturally. Device isolation is enabled here.
- The IoT VLAN. This is my smart plugs, WiFi bulbs, Google Nest devices, TVs, etc.
The reason for separating the IoT devices from everything else has to do with security. Some of these devices are cheap smart plugs and even smart bulbs. Some of these are from overseas companies I’ve never even heard of before. That’s on me for using these instead of stuff from a more reputable brand, but still. Who knows what any of these devices are doing or watching on the network. I’ve mentioned before I have some Google Nest devices. Are these snooping on my network, sending network usage patterns back to Google? Who knows.
Anyway, most of these IoT devices require WiFi. So I created a new WiFi SSID and attached the IoT VLAN to it. I don’t necessarily know if it increases security, but I also set it as a hidden network. At the very least, since I live in a sizable apartment complex, I didn’t want to further clutter up an already cluttered SSID list. That said, there are one or two devices that are wired, such as TVs. For those, I had to tag ports on the appropriate switches. That’s one area I would like to play with more: port tagging. However, since I’m using some of the more basic Unifi gear, there are some limitations.
Fom there, I merely had to place the networks in the correct zones. I created a new IoT zone and then moved the IoT VLAN into it. My Main network is in the out-of-the-box Internal zone. And when I created a Guest WiFi network, Unifi automatically placed it in the Hotspot zone, with the proper firewall rules to isolate the network (devices on the Guest network are also isolated from each other).
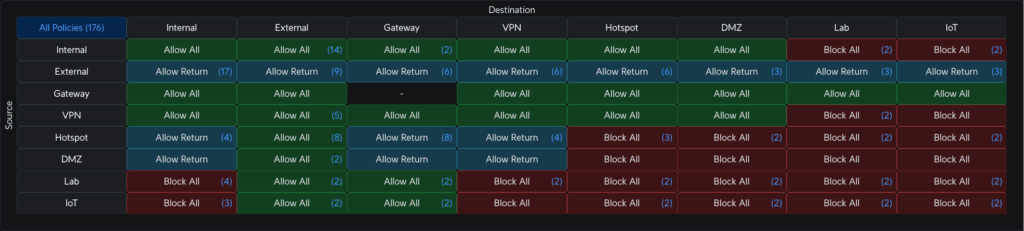
By default, user-created zones in Unifi are automatically isolated from other networks (though they’ll always at least have Internet access, which is in the External zone). So creating the IoT zone did most of the work for me. I didn’t have to create all these rules to isolate it from other zones. However, I wanted devices in the Internal zone to be able to communicate to devices in the IoT zone. Two reasons for this:
- If I lose Internet access, I want some limited control over IoT devices. I don’t want to have to press the power button on my smart switches if I want to turn them on/off; I want to be able to use my phones and apps.
- I have a Chromecast and a few other devices that I can cast media to. I moved those devices to the IoT VLAN, but of course my computers and phones will remain on the Main VLAN.
However, if a device is communicating “down” to devices in the the isolated IoT VLAN, there needs to be some ability to communicate “up” as well. If I ping from Main to IoT, that only works if IoT can respond back. But I don’t want to devices from IoT able to initiate and maintain connections to Main.
Luckily, Unifi makes this easy—though I had to ask around and play around a lot to figure this out.
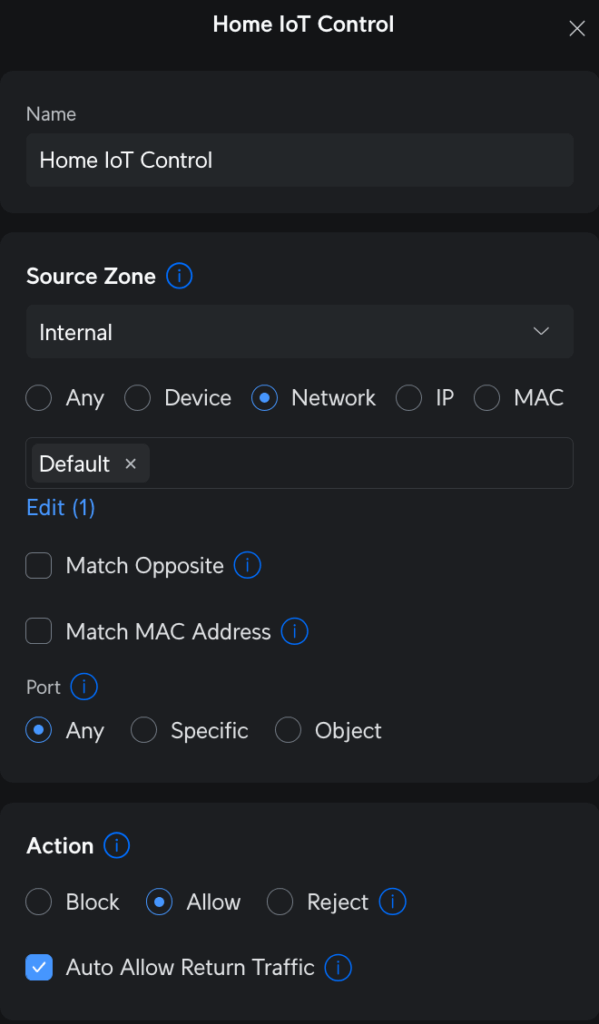
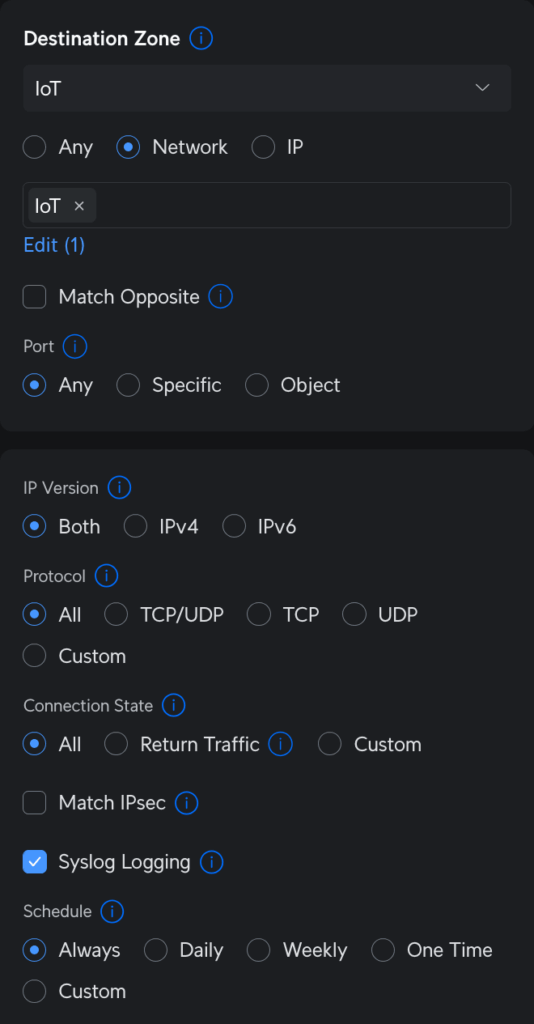
One single rule in the “source Internal, destination IoT” part of the zone matrix can be made to allow this behavior. On the source side, I selected the Main (Default) network in the Internal zone to allow connections on any port. On the destination side, I have the IoT network in the IoT zone. The most important thing here is, on the source parameters, that checkbox to “Auto Allow Return Traffic.” When the rule is saved, that checkbox creates a corresponding partner rule in the “source IoT, destination Internal” part of the matrix to allow only traffic from IoT only if Internal initiated first.
Essentially, I can ping from Main to IoT, but I can’t ping from IoT to Main. This works because the “bottom” rule, or broadest firewall rule, in the IoT zone, disallows traffic to/from any other zones. Like I said before, that’s Unifi’s default behavior for new zones. My rule creates an exception to the policy.
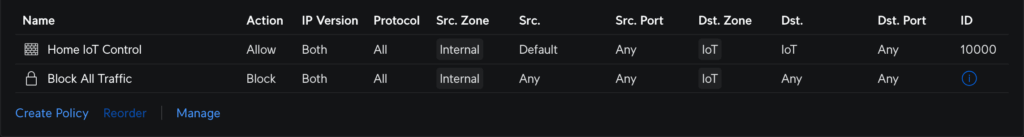
I tested everything out afterwards, and the results were mixed. I disconnected my network from the Internet to see how different applications would react. From my cell phone (also only on WiFi), I could easily still control the smart plugs, which is exactly what I wanted.
But the media casting wasn’t as successful. The Chromecast seemed to accept casting from a computer via direct network connection, but Spotify on my phone didn’t quite work with my Google Nest speakers without Internet. Not ideal, but I don’t cast that much anyway. The main thing is controlling my lighting.
With this finally done, I feel like my basic network setup is essentially complete. There’s always more that I could tweak. For example, I have a printer. Maybe I put the printer on its own VLAN and allow any device in any network the ability to print to it. Right now, it sits in the Main VLAN with my computers. I don’t have that many guests, so it’s really NBD.
But for now, this is good. Time to move onto something else.